The Delegation of Authority/Accountability
I discussed the delegation of authority being the core concept behind SOX. Note here that the flip side of the management’s authority, delegated by the company shareholders (through the board of directors), must be their accountability to the BoD/shareholders.
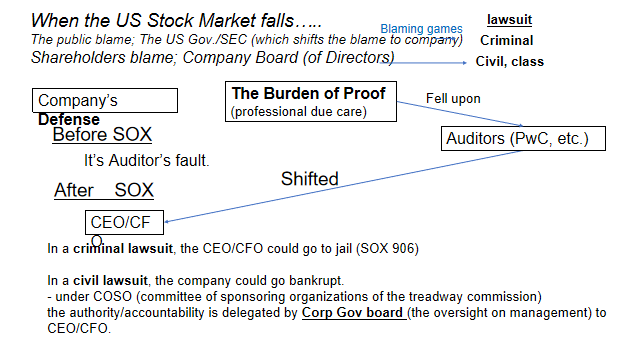
SOX 302 requires company CEO/CFO to certify the effectiveness of their internal controls.
This, then, naturally necessitates them to delegate the accountability to process/control owners, when it comes to process level controls (PLC’s), at a department management level. Accordingly, a public company needs to design the PLC’s in such a way as to hold adequately competent management accountable for relevant, underlying (financial) data (which would affect related journal entries ultimately posted to the accounting ledgers).
At the same time, strong leadership is necessary to hold financial control team accountable for SOX compliance, and for the team to;
1. adopt the “top-down, risk-based” approach properly per Auditing Standards No. 5;
2. be able to define logical key risks (with relevant financial assertions) in each of the five phases from Initiation through Reporting, including the critical paths at which journal entries are recorded/posted to the sub-ledger/GL;
3. be able to support business departments to identify proper control owners for each proper, effective key controls, which mitigate each of the logically-defined key risks;
4. design Preventive controls, as opposed to Detective controls, to the extent possible;
5. provide stakeholders, including external auditors, with the legitimate rationality for the U.S. Company’s assessment of PLC’s under SOX; and
6. sustain CFO’s (and CEO’s) certification in the financial statements.
The Detective vs. Preventive Controls
The number 4 above is particularly important to keep in mind when designing controls because;
even if a Detective control was effective (and a misstatement was corrected thanks to the effective control), the misstatement would repeat as the root cause for the misstatement has not been rectified.
That’s why designing Preventive controls (e.g., application/access controls, management review of data input, etc.), as opposed to Detective controls (e.g., management review of reconciliation, etc.) effectively is important to design and operate the controls that are “effective” under SOX 404.
For a more detailed discussion about designing Preventive controls, see this post.